The Millennium Alliance is proud to introduce its 2020 Advisory Board. This year, the board welcomes ten new industry leaders to join their peers who have shown their dedication to professional growth and education. These new members are invited to join existing members in contributing their knowledge and experience to the ongoing conversations and partnerships within the Advisory Board and The Millennium Alliance community that cultivate business transformation and executive education.
Created in 2017, The Advisory Board is a group of world-renowned industry leaders and visionaries who are tasked with providing invaluable input and expertise. The Board’s main task is to ensure that The Millennium Alliance continues to deliver the highest level of Education, Transformation and Leadership to our members.
“The Millennium Alliance has experienced remarkable growth over the last six years, which has been fueled by the continued support of our Advisory Board members. Bringing together such an elite group of world-renowned leaders to provide us with their invaluable input and expertise, allows us to take innovative thinking and peer-to-peer learning to a whole new level for our members and partners.” – Alex Sobol, Co-Founder & Managing Partner, The Millennium Alliance
Given their wealth of knowledge and invaluable insight, we urge our members and partners to connect with our Advisory Board members on Linkedin.
Here you’ll see our full Board of Healthcare, Marketing, Digital Enterprise & Cybersecurity experts, with each member’s feature clicking through to their respective Linkedin pages. We’re thrilled and honored to see our Advisory Board grow this year, and we’d like to highlight our newest members for 2020.
Brad Wilson, Healthcare Expert
Brad Wilson is CEO Emeritus of Blue Cross Blue Shield of North Carolina, Executive in Residence at Wake Forest University and holds an adjunct faculty position at UNC-Chapel Hill.
Prior to joining BCBSNC he served as General Counsel to NC Governor James B. Hunt and practiced law for 14 years. A dedicated public servant, Brad has Chaired many Gubernatorial, Attorney General and Judicial Commissions. He also served on the UNC System Board of Governors for 16 years and Chaired that Board for 4 years during his tenure. Brad is the recipient of the Order of the Long Leaf Pine, the highest civilian honor in North Carolina. A lifelong North Carolinian, he earned a BA from Appalachian State University, JD from Wake Forest School of Law and an MA from Duke University.
Patrick Carroll, Healthcare Expert
Dr. Carroll is a physician leader with experience in retail health, workmen’s compensation, Medicare and commercial risk programs, integrated delivery networks, managed care and primary care practices. He has led groups in value-based care transformation in the era of global risk payment. He has extensive experience in retail health, ACO/MSSP development, and execution in a variety of settings: the Indian Health Service, Medical Director at Tufts Health Plan, a large innovative multispecialty group at Atrius Health, CMO in a 3 billion dollar fully integrated health system at Hartford Healthcare, Group Vice President /CMO Walgreens and currently CMO at HIMS-HERS.
Steve Allen, Healthcare Expert
Steve Allen, MD, MBA was the Keynote Speaker at our most recent Healthcare Providers Transformation Assembly this November. He is the recently retired CEO of Nationwide Children’s Hospital, a preeminent academic medical system in Columbus, Ohio. When he joined Nationwide Children’s in 2006, the hospital was known as an important regional health care center. By the time of his retirement in July of 2019, Nationwide Children’s had become one of the country’s most respected and innovative pediatric institutions with over $2.4 billion a year in revenue. It now consistently appears on U.S. News and World Report Honor Roll list of America’s top 10 children’s hospitals, and its Abigail Wexner Research Institute is one of the National Institutes of Health’s top-funded freestanding pediatric research facilities. Dr. Allen oversaw a period of unprecedented growth and transformation in Nationwide Children’s size, scope, and vision. In the process, he has become one of the most prominent voices in American pediatric health care strategy and policy.
Chris Carroll, Marketing Expert
Chris has over 30 years of marketing and management success, including very substantial restaurant experience on both the client and agency sides of the ledger. Chris has spent over 9 years with the Subway Restaurant brand over two different periods. First from 1999 until 2005 when he led the Franchisee Marketing Trust. During this period same-store sales grew by almost 50% while doubling the number of locations globally. Chris was asked to come back to Subway in 2015 during the transition of leadership from founder Fred Deluca to his sister Suzanne Greco. After leaving Subway in 2005, Chris served for several years as Chief Marketing Officer for Cosi Restaurants, overseeing marketing, restaurant design and menu development. Chris is currently forming a consulting practice focused on working with brands large and small to focus Brand Strategy and activate guest engagement., Chris has over 30 years of marketing and management success, including very substantial restaurant experience on both the client and agency sides of the ledger. He is now a partner in Brand Equity Ventures, providing inspirational leadership and success domestically and globally.
David Sable, Marketing Expert
Formerly Global CEO of Y&R, David has led and helped unify a number of their global businesses and worked on many of their major clients. He is known for his creativity, content, strategic innovation and impactful partnerships. A leading industry thought leader, published author, and early digital pioneer, David is a regular contributor to LinkedIn and is a sought-after keynote and inspirational speaker David was selected as both a Top 20 Must-Know Global Influencer by LinkedIn, as well as a Top 10 Most Generous Marketing Geniuses by Fast Company. Passionate about giving back, he serves on the Board of the Special Olympics, UNICEF and UNCF and, in the commercial world, he sits on the Board of Directors of American Eagle Outfitters’. World traveler. Gamer. Die-hard Doors fan. Grandfather. Hippie at heart.
Prashant Malaviya, Marketing Expert
Prashant Malaviya is an Associate Professor of Marketing and Senior Associate Dean of MBA Programs. He came to Georgetown in 2008 after nine years at INSEAD, France. Prior to INSEAD, he held an appointment at the University of Illinois at Chicago, and visiting professorships at the Wharton School, as the Titan Industries Professor at ALBA Graduate Business School in Athens, Greece, and at the Kellogg School of Management. Professor Malaviya is a Consumer Psychologist by training and received his Ph.D. from the Kellogg School of Management at Northwestern University. His research focuses on understanding how consumers use the information to make product judgments and consumption decisions. His research has been published in leading marketing journals including, Journal of Consumer Research, Journal of Consumer Psychology, Journal of Marketing, Journal of Marketing Research, Journal of Personality and Social Psychology, and Psychology & Marketing. He has taught courses to Executives, MBA and Undergraduate students on marketing management, marketing strategy, brand management, customer focus, consumer behavior, and related topics. He was awarded the Emerald Citation of Excellence for publishing “one of the top 50 management articles in 2007,” was a finalist for the Best MBA Core Teacher award at INSEAD and was named Outstanding Reviewer by the Journal of Consumer Research. He currently serves on the editorial review board of the Journal of Consumer Psychology. Prior to entering the world of academia (and consumers), Professor Malaviya worked in India as an engineer at Tata Motors and as a marketing analyst at Nestlé.
Dawn Lerman, Marketing Expert
Dr. Dawn Lerman is Executive Director of the Center for Positive Marketing and Professor of Marketing at Fordham University’s Gabelli School of Business. She is a consumer psychologist—passionate about studying the impact of words and language on brand perceptions, consumer-brand relationships and memory for brands— and is the author of the book The Language of Branding: Theories, Strategies, and Tactics. Dr. Lerman serves on the editorial review boards of the Journal of Business Research and the International Marketing Review and is an active member of the board of directors of the ANA Educational Foundation (AEF). She is also a designated " Thought Leader” and regular speaker for the CMO Assembly of the Millennium Alliance, a leading technology, business, and educational advisory firm headquartered in Midtown Manhattan. Prior to arriving at the Gabelli School, Dr. Lerman served in a leadership role at The Ferolie Group, a leading New York-area food broker, where she managed several major brands such as Van Den Bergh Foods, Kraft, Apple & Eve, McCormick and the James River Corporation. She holds a Ph.D. and M.Phil. from the City University of New York, an MBA from New York University’s Leonard N. Stern School of Business, and a BA in French language and literature from Brandeis University.
Rhonda Vetere, Digital Enterprise Expert
Rhonda is the EVP, Chief Information Officer at Herbalife Nutrition. She is an established global leader in the technology industry, with over 25 years of experience working internationally across industries, from telecom to banking to beauty to health. In her tenure as Chief Technology Officer at Estée Lauder Companies, Rhonda spearheaded the transformation of the IT capabilities foundation into a digital environment at record industry pace, without business disruption, around the world – while saving $28 million a year. Prior to Estée Lauder Companies, Rhonda worked in leadership roles at AIG, HP Enterprise Services, Barclays, and JPMorgan Chase. Rhonda has been recognized for her leadership and influence, notably with a 2019 Most Powerful 50 Women in Technology by the National Diversity Council, 2019 Human Forward Award by Randstad, 2017 Stevie Award for Excellence in Transforming Business, and several Top 100 CIO/CTO Leaders in STEM awards. She contributes her perspective and knowledge by serving on boards for professional, educational, and athletic institutions, including The Canadian Cloud Council, Longwood University, George Mason University School of Business, SWAAY Magazine, Miss Fashion Week, and Xcelocloud Inc. An avid athlete, Rhonda regularly races in triathlons, half-marathons, marathons, and IRONMAN 70.3 mile triathlons as well as mentors students, young athletes, and women through sports. For two years in a row, she has run 55 miles across the Serengeti as part of a fundraiser for local female empowerment programs.
Sean Ammirati, Digital Enterprise Expert
Sean Ammirati is a Professor of Entrepreneurship at Carnegie Mellon University’s Tepper School of Business. In addition to teaching, he is also the Co-Founder and Director of the Carnegie Mellon Corporate Startup Lab (CSL). The CSL is a Swartz Center initiative that has conducted research and developed tools to help companies better adapt and integrate entrepreneurial best practices into their own innovation processes. In addition to his work at CMU, Sean also joined Birchmere Ventures as a Partner in 2012. Birchmere focuses on seed-stage SaaS and marketplace startup investments. Prior to joining Birchmere, Sean spent 12 years founding, building and selling businesses in the software and media industries. He was Chief Operating Officer of ReadWriteWeb acquired by the private-equity rollup SAY Media to strengthen its technology channel. Prior to that, Sean was the co-founder and CEO of mSpoke, which was LinkedIn’s first acquisition. His first startup was Peak Strategy, which was acquired by Morgan Stanley. He recently completed his first book The Science of Growth, which was released by St Martin’s Press in April 2016 and was subsequently translated and published in Korean and Mandarin. Finally, Sean is also the host of one of the most popular podcasts on corporate innovation – Agile Giants which you can find on your favorite podcasting platform.
Phil Fasano, Digital Enterprise Expert
Phil Fasano is a visionary thought leader, award-winning corporate executive, and Fortune 500 board-level business strategy expert who brings more than 20 years of experience in the financial services, technology, insurance, and healthcare industries. He is widely respected as an expert on technology innovation, risk management, financial growth and oversight, corporate governance, cybersecurity, and public policy, among others. Currently serving as Chief Executive Officer at Bay Advisors LLC, a strategic advisory firm he founded, Fasano is considered an influential voice in the push to evolve how companies create, market and use technologies to transform future growth and profitability. Fasano has been interviewed and quoted by numerous prestigious national media, including Forbes, Fortune, The Wall Street Journal, Reuters, The New York Times, CIO Magazine, US News and World Report & InfoWorld among many others. Fasano was inducted to the CIO Hall of Fame, the summer of 2017. In his spare time, you will find Phil enjoying life with family and good friends. He lives in Virginia and Northern California with his wife, Judy and five adult children.






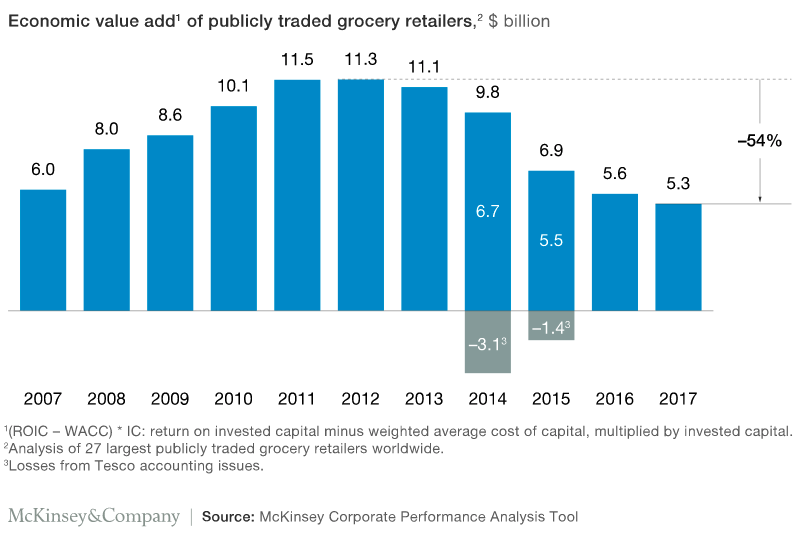 What’s happening in grocery retail is more than a shakeout, and retailers can certainly expect to see further upheaval in the coming decade. In fact,
What’s happening in grocery retail is more than a shakeout, and retailers can certainly expect to see further upheaval in the coming decade. In fact, 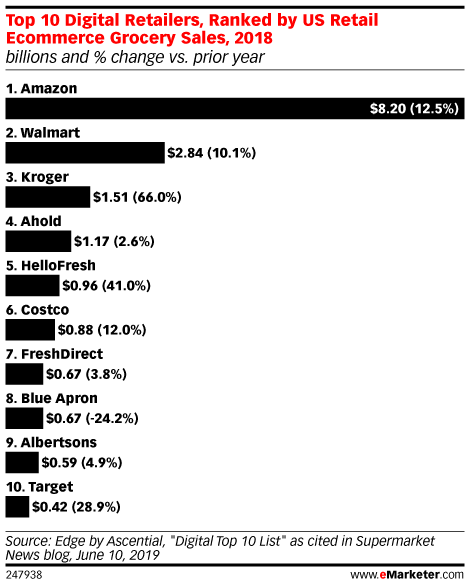












 With
With